Having fun with science and technology.
Monitoring internet censorship with Tor
2008-04-12
You have probably heard already of Tor, a tool for surfing the internet anonymously. It can also be used to evade censorship, but less known is the fact that you can turn the tables and monitor internet censorship in various parts of the world. Not only that, you can use Tor to visit websites pretending you come from almost any country.
First of all, let me briefly reviews how Tor works. Basically, you send a request to one server of the Tor network, which passed it on to another, then another, and at the end of the chain the last server sends the request to the final destination (e.g., a web site you'd like to visit). The location of the last server ("exit node" in Tor terminology) is the important thing here. By selecting a specific exit node, you will see the internet just as people directly accessing content from there.
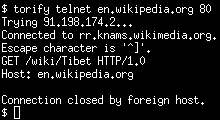 |
Chinese censorship in action: access to Wikipedia's article on Tibet is blocked |
For example, you can select a Chinese exit node and look how much the internet gets censored. You can make lists of blocked content, study how the bans change over time or learn something about the filter techniques. As you can see from the screenshot, the Chinese government uses forged TCP RST packets to block content. Some tests revealed the while access to the English Wikipedia often works, requesting articles with inconvenient content like the article on Tibet is always being blocked. Accessing the Chinese version of Wikipedia is never possible.
So how is it done? First of all you need to know which exit nodes run in the country you are interested in. There are several websites containing the information (e.g. here, here and here). Look for the name of the exit node you are going to use. Next, open your torrc file and add the following two lines:
StrictExitNodes 1
ExitNodes $name
Of course, replace $name by the name of your desired exit node. You can also supply multiple exit nodes to choose from by adding them separated with commas. Now restart Tor and use the network as usual.
You can use this method not only to monitor censorship. Other useful examples for using Tor as a method to access websites from a different origin include bypassing restrictions on the location. For example, the infamous BBC iPlayer not only requires a proprietary operating system, but also checks whether your request comes from the UK. Thanks to Tor, you can at least overcome the second hurdle.
Copyright 2006--2011 Hendrik Weimer. This document is available under the terms of the GNU Free Documentation License. See the licensing terms for further details.